In today’s digital age, maintaining online privacy and security is more critical than ever. The Tor network stands as a cornerstone in safeguarding users’ anonymity and providing a safe space for internet browsing. If you’re wondering, “What is Tor and how does it work?” you’re in the right place. In this article, we’ll explore the ins and outs of the Tor network, how it ensures secure browsing, and why millions of users trust it.
What is the Tor Network?
The Tor network is a free, open-source system designed to help users browse the internet anonymously. By masking your IP address, it ensures that your browsing activity is not traced back to you, making it a powerful tool for protecting privacy online. The name “Tor” stands for The Onion Router, which reflects the network’s layered approach to encryption and data routing.
How Tor Network Works: Layered Encryption Explained
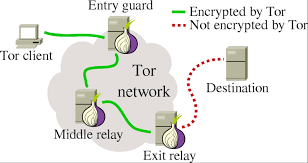
One of the key features that make the Tor network stand out is its use of layered encryption. This process is often compared to the layers of an onion, hence the name. When you connect to the Tor network, your internet traffic is routed through multiple relays (also called nodes), which encrypt your data multiple times.
Here’s a step-by-step breakdown of how it works:
- Data Entry: When you access a website through the Tor network, your data first passes through a local relay.
- Layered Encryption: The data is encrypted multiple times as it moves through several layers, each time by a different relay in the network.
- Random Path: The Tor network chooses a random path through a series of relays, making it difficult for anyone to track the origin of the data.
- Final Decryption: When the data reaches the final relay, all encryption layers are peeled off, and the data reaches its destination.
This process ensures that even if someone is monitoring traffic, they cannot trace the connection back to the original user.
Benefits of Using the Tor Network
The Tor network offers several benefits, primarily revolving around privacy and freedom:
- Anonymity: Users can browse the internet without revealing their identity or location.
- Access to Restricted Content: Tor allows you to access websites and content that may be restricted or censored in certain countries.
- Protection Against Surveillance: It shields your browsing from government surveillance or unwanted tracking by corporations.
These features make it a valuable tool for privacy-conscious users and those seeking to protect themselves from prying eyes.
Why You Should Consider Using Tor
Whether you’re concerned about surveillance, want to access geo-blocked content, or just prefer to keep your browsing activity private, the Tor network is an excellent choice. Its encrypted, decentralized nature provides a strong defense against online threats.
If privacy matters to you, Tor allows for secure browsing while maintaining anonymity, making it an essential tool for many.
Frequently Asked Questions
1. What is the Tor network? The Tor network is an anonymous browsing system that helps users hide their online identity by encrypting and routing internet traffic through multiple relays.
2. How does the Tor network protect my privacy? The Tor network encrypts your internet traffic through several layers of encryption, making it nearly impossible for anyone to track your browsing activity or pinpoint your real-world identity.
3. Why should I use the Tor network? You should use the Tor network if you value your online privacy, want to access restricted content, or seek protection from surveillance. It ensures that your identity remains hidden while you browse the internet.
4. Where can I access the Tor network? The Tor network can be accessed by downloading and installing the official Tor browser from the Tor Project’s website.
5. How does Tor differ from a VPN? While both Tor and a VPN offer privacy protection, Tor routes traffic through multiple relays and is entirely free, whereas VPNs typically involve paid subscriptions and route traffic through one server.
6. Will using Tor make me completely anonymous? While Tor significantly enhances your anonymity, it’s important to use it responsibly. Avoid logging into personal accounts and refrain from sharing identifying information to maintain maximum privacy.