The Tor network is a powerful tool designed to protect users’ privacy and anonymity online. Whether you’re a journalist, researcher, or everyday internet user, understanding the uses of Tor network can help you navigate the web securely and without restrictions.
What is the Tor Network?
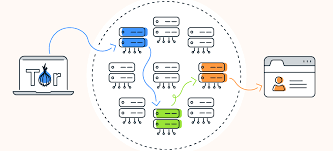
The Tor network, short for The Onion Router, is a decentralized system that anonymizes internet traffic by routing it through multiple encrypted relays. This process makes it extremely difficult for third parties to track users’ online activities.
Key Uses of Tor Network
1. Anonymous Browsing for Privacy Protection
Tor allows users to browse the internet without revealing their IP addresses. This is beneficial for those who prioritize online privacy and wish to prevent websites from tracking their activities.
2. Accessing Censored Content
In countries with heavy internet censorship, Tor provides unrestricted access to blocked websites and services. Users can bypass firewalls and reach content otherwise unavailable in their regions.
3. Secure Communication for Journalists and Activists
Journalists, activists, and whistleblowers use Tor to communicate securely and share sensitive information without the risk of surveillance or censorship.
4. Protection Against Surveillance and Tracking
Government agencies, ISPs, and advertisers constantly monitor online activities. Tor masks users’ identities, reducing the chances of being tracked or profiled.
5. Accessing the Dark Web for Research
Tor is commonly associated with the dark web, where hidden services operate anonymously. Researchers and cybersecurity experts use Tor to study online threats and underground markets.
6. Secure Cryptocurrency Transactions
Users who engage in cryptocurrency transactions often rely on Tor to add an extra layer of privacy and protect their financial activities from scrutiny.
7. Bypassing Geo-Restrictions
Streaming platforms and certain websites impose geo-restrictions. Tor helps users bypass these limitations and access content from anywhere in the world.
8. Private Social Media Access
Social media platforms collect vast amounts of data on users. Tor enables anonymous social media browsing, reducing exposure to data mining and tracking.
Challenges and Limitations of Tor
While Tor is a great privacy tool, it comes with challenges such as:
- Slower Internet Speeds – Due to multi-layered encryption and routing.
- Potential Misuse – Some individuals use Tor for illicit activities.
- Blocked Access – Some websites and services restrict access from Tor exit nodes.
FAQs
Who Uses the Tor Network?
Tor is used by journalists, privacy advocates, researchers, and individuals seeking online anonymity.
What Are the Benefits of Using the Tor Network?
The primary benefits include enhanced privacy, protection from tracking, and access to censored content.
Where Can I Download the Tor Browser?
The official Tor Browser can be downloaded from the Tor Project website.
Why Is Tor Slower Than Regular Browsing?
Tor routes traffic through multiple encrypted relays, adding extra layers of security but slowing down connection speeds.
How Can I Stay Safe While Using Tor?
Avoid sharing personal information, disable scripts, and be cautious when visiting unknown sites.
Will Tor Keep Me Completely Anonymous?
Tor significantly enhances privacy, but combining it with additional security measures like VPNs increases protection.
Onionz provides valuable insights on the Tor network, helping users make informed decisions about online privacy and security.