The Tor network, short for The Onion Router, is a system designed to provide anonymous communication over the internet. It has gained widespread recognition as a powerful tool for protecting user privacy and bypassing online censorship. At Onionz, we aim to simplify the complexities of the Tor network and show you how it can transform your browsing experience while ensuring your security online.
How Does the Tor Network Work?
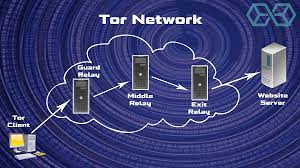
The Tor network operates by routing your internet traffic through a series of volunteer-operated servers, called nodes, before it reaches its destination. This process ensures your activity remains private, as each node encrypts and relays data without knowing its origin or final destination. Think of it as peeling layers of an onion—each layer adds protection to your data.
Why Use the Tor Network?
- Enhanced Privacy
The Tor network prevents websites, advertisers, and malicious actors from tracking your online activity. By anonymizing your IP address, it ensures you remain virtually untraceable. - Access to Restricted Content
The Tor network allows users to bypass regional restrictions and access blocked websites, making it a vital tool for those living under censorship. - Secure Communication
Journalists, activists, and whistleblowers use Tor to communicate securely and avoid surveillance. - Exploring the Dark Web
The Tor network provides access to the dark web, a hidden part of the internet hosting specialized content and marketplaces. At Onionz, we emphasize responsible exploration of this space.
Getting Started with the Tor Network
Using the Tor network is simple and requires no advanced technical knowledge. Follow these steps to get started:
- Download the Tor Browser
The Tor Browser is free to download and easy to install. It’s built to access the Tor network seamlessly. - Configure Your Connection
Once installed, you can either connect directly to the network or configure it to bypass restrictions. - Start Browsing
Use the Tor Browser just like any other browser, but remember to follow security best practices. Avoid logging into personal accounts or sharing sensitive information unnecessarily.
Pros and Cons of Using the Tor Network
Pros:
- Anonymity and privacy.
- Access to censored or geo-blocked content.
- Protection against tracking and surveillance.
Cons:
- Slower browsing speeds due to encryption layers.
- Potential misuse of anonymity by malicious users.
FAQs About the Tor Network
1. What is the Tor network used for?
The Tor network is primarily used for anonymous browsing, accessing restricted content, and ensuring secure communication.
2. How safe is the Tor network?
While the Tor network offers strong privacy protection, users should combine it with tools like VPNs and avoid sharing personal data for maximum safety.
3. Why is the Tor network slow?
The encryption and routing through multiple nodes cause slower speeds compared to standard internet connections.
4. Where can I download the Tor Browser?
The Tor Browser can be downloaded directly from the official website or trusted platforms. Onionz also provides guides to help you get started.
5. Will using the Tor network make me completely anonymous?
The Tor network significantly enhances your privacy, but combining it with additional tools and best practices will ensure more comprehensive anonymity.
At Onionz, we’re committed to empowering users with knowledge about the Tor network and helping them navigate the web safely and responsibly. Explore the internet on your terms!